


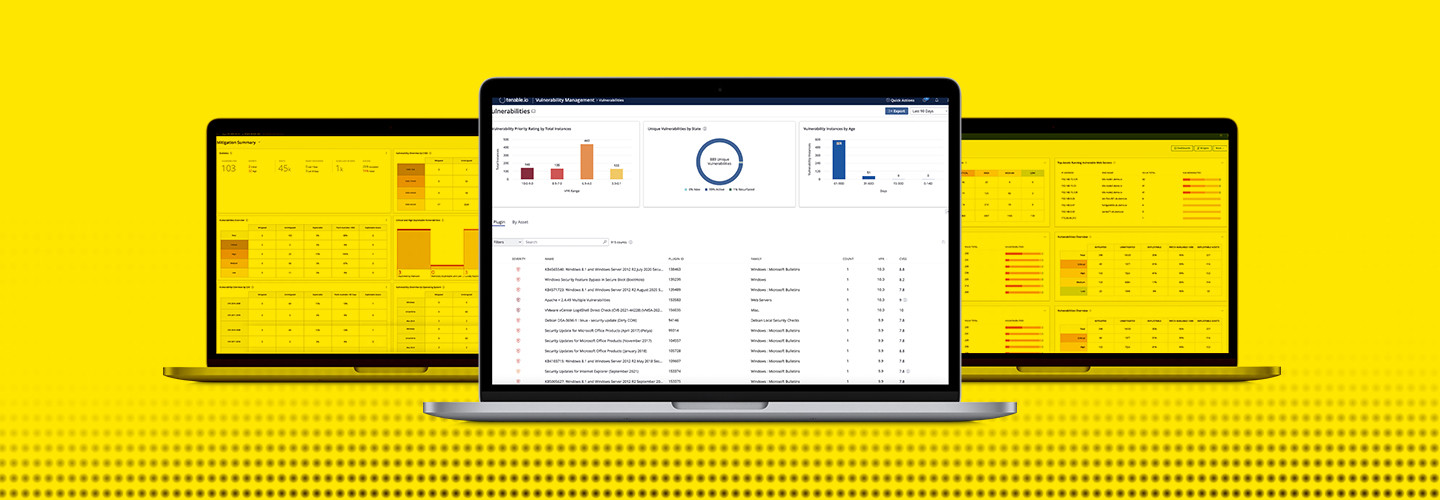
In the ever-evolving landscape of cybersecurity, organizations face the constant challenge of protecting their IT systems from vulnerabilities. Two companies, Tenable and Morphisec, have emerged as leaders in enhancing vulnerability management capabilities.
Tenable, utilizing data science, threat feeds, and artificial intelligence, has developed an innovative approach to prioritize and fix vulnerabilities. Their platform predicts which vulnerabilities require immediate attention by calculating the impact and ease of exploitation for each vulnerability. With an accurate Vulnerability Priority Rating score, Tenable provides users with a clear understanding of the most critical vulnerabilities. Their user-friendly dashboard and reports enable organizations to allocate their limited resources effectively.
On the other hand, Morphisec addresses the limitations of current vulnerability management practices driven by the Common Vulnerability Scoring System (CVSS). They have developed a risk-based vulnerability prioritization capability that combines threat intelligence with business context and usage data. Morphisec's approach includes business context risk prioritization, host exposure scoring, application-driven risk prioritization, exploit prediction scoring, continuous usage-based scoring, and patchless protection using Automated Moving Target Defense (AMTD) technology. By proactively blocking advanced and evasive attacks, Morphisec's AMTD technology provides organizations with an added layer of defense.
Both Tenable and Morphisec offer valuable solutions to help organizations proactively address vulnerabilities and protect their IT systems. By leveraging data science, artificial intelligence, and risk-based prioritization, these companies empower organizations to stay one step ahead of cyber threats.
In an interview with Michael Gorelik, CTO and Head of Malware Research at Morphisec, he discusses the business impact of vulnerabilities and the challenges organizations face in vulnerability prioritization. He emphasizes the importance of understanding the business context and potential exploitability of vulnerabilities. Adhering to regulatory frameworks like GDPR aids in vulnerability prioritization and maintaining an organization's credibility. Automated systems for vulnerability prioritization address the challenges of manual methods by providing continuous and current data. Incomplete asset inventories and data pose challenges in vulnerability prioritization, and organizations can overcome these by mapping high-risk assets and applying compensatory controls. Key factors in building a vulnerability prioritization formula include business context, exposure of hosts, vulnerabilities on applications, and exploitability. The future of vulnerability prioritization is heading towards exposure management, which encompasses a broader range of risk elements.
[24e65f3b]
[0eba848c]
[497d6778]
[0aa1b169]