




A new malware known as Perfctl has been identified, targeting over 20,000 misconfigurations in Linux servers for the past three to four years. Researchers from Aqua Nautilus estimate that it may affect millions of servers worldwide. This malware employs rootkits to maintain stealth, ceasing its activity when users log in, and utilizes TOR for external communication. Perfctl exploits the Polkit vulnerability (CVE-2021-4043) to escalate privileges, allowing it to execute its main payload, a packed ELF binary (MD5: 656e22c65bf7c04d87b5afbe52b8d800). The malware is particularly associated with cryptomining activities, specifically using the XMRIG mining software. The discovery of Perfctl was made through incident reports in community forums, highlighting the ongoing risks posed by such stealthy malware. Its architecture includes deceptive naming conventions designed to evade detection, making it a significant threat to Linux server security. Detection methods for Perfctl include monitoring for CPU usage spikes and identifying unusual binaries. To mitigate the risks posed by this malware, experts recommend patching vulnerabilities and restricting file execution on affected systems. [5fbdc118]
In light of this new threat, the existing vulnerabilities in the Linux kernel and other systems are further compounded. A recent vulnerability in the Linux kernel has been flagged by the Federal Office for Information Security (BSI), which warned that multiple vulnerabilities could be exploited by local attackers. The risk level is assessed as 'medium' with a CVSS score of 6.6. Users are urged to keep their systems updated to mitigate these risks. [9cc92b7e]
Additionally, a failed Linux backdoor attempt was discovered in XZ Utils, which could have led to a major cyberattack on corporate servers. Open-source leaders are urging maintainers to be vigilant against social engineering attacks that may target open-source projects. [1589f957]
Intel has disclosed two vulnerabilities in its AI model compression software, with the first vulnerability (CVE-2024-22476) allowing remote code execution with a CVSS score of 10. Users are advised to update to version 2.5.0 or later to mitigate these risks. [e187c66d]
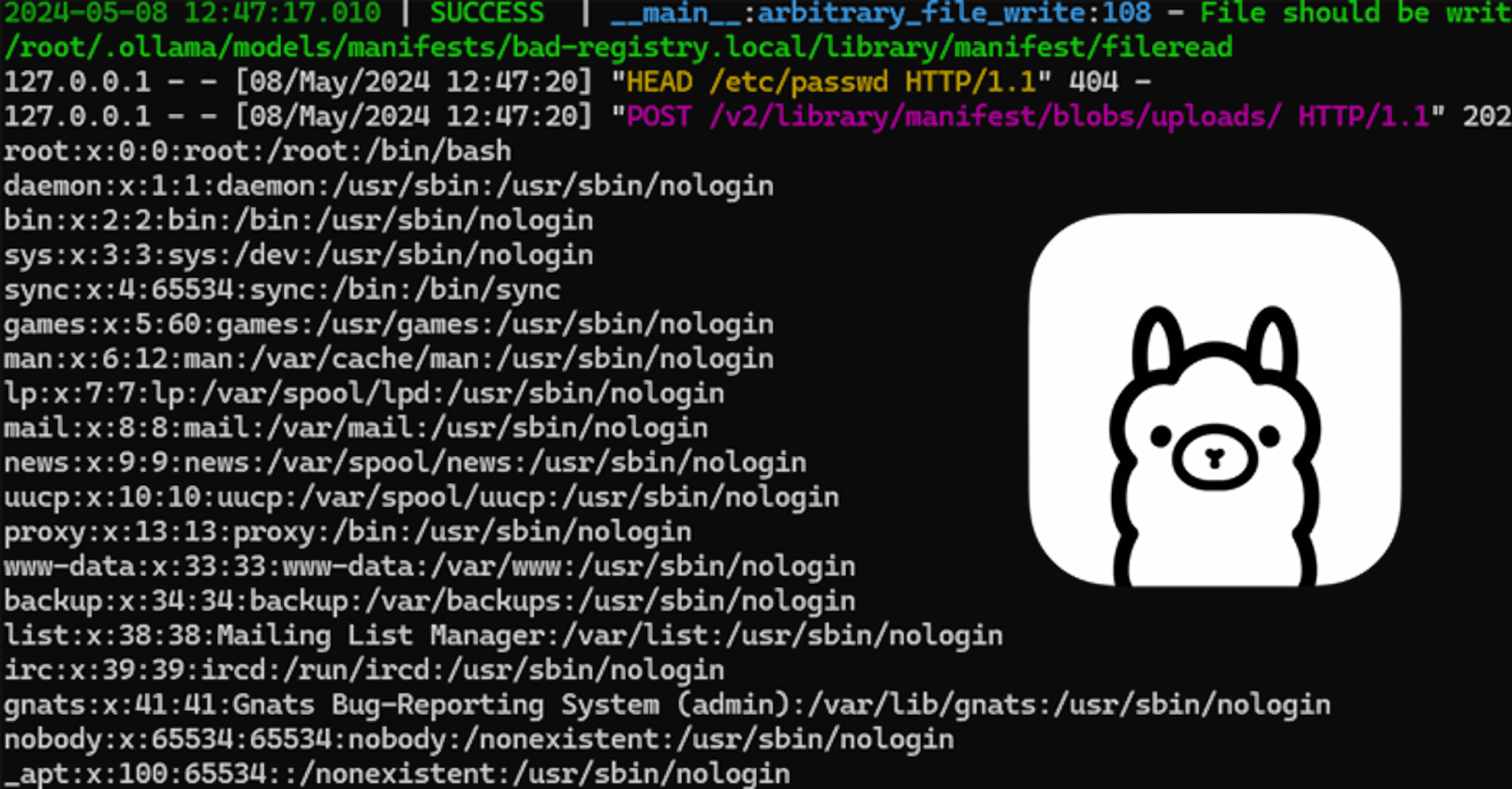
Moreover, the Ollama AI platform faced a critical vulnerability (CVE-2024-37032) that allowed remote code execution due to insufficient input validation. This vulnerability was particularly severe in Docker installations and has since been fixed. [02e5b439]
Finally, a vulnerability known as Sinkclose has been found in AMD chips, affecting virtually all AMD processors since 2006. This flaw allows hackers to run their own code in the System Management Mode, posing a significant risk to system integrity. AMD has acknowledged the issue and provided mitigation options. [c0162c9b]